How does the Firewall Work?
What is the Firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls can be implemented as hardware appliances, software applications, or a combination of both. They are designed to protect networks from malicious activities such as unauthorized access, data theft, malware attacks, and other cyber threats. Firewalls provide an additional layer of security that helps organizations protect their data and resources from malicious actors on the internet.
Hardware Firewalls
Hardware firewalls are essential components of an organization’s security architecture, as they provide a physical barrier to protect the network from external threats. By using hardware firewalls, organizations can protect their networks from malicious attacks and unauthorized access. In addition, hardware firewalls can be used to monitor traffic and enforce security policies. With the right hardware firewall in place, organizations can ensure that their network is secure and their data is protected.
Software Firewalls
Software firewalls are a type of security tool that helps protect your computer from malicious software and other online threats. They act as a barrier between your computer and the internet, monitoring all incoming and outgoing traffic to ensure that only secure connections are allowed. By preventing unauthorized access to your system, software firewalls can help keep you safe from hackers, malware, spyware, and other malicious activities. Additionally, they can also be used to block certain types of content or websites that you don’t want to be exposed to. Software firewalls can provide an extra layer of protection for your system and data, so it’s important to make sure you have one installed on your computer.
Firewalls use different methods to protect your network or computer. They include the following:
Packet Filtering
Data is organized in packets. When a firewall executes packet filtering, it examines the packets of data, comparing them against filters, which consist of information used to identify malicious data. If a data packet meets the parameters of a threat as defined by a filter, then it is discarded and your network is protected. Data packets that are deemed safe are allowed to pass through.
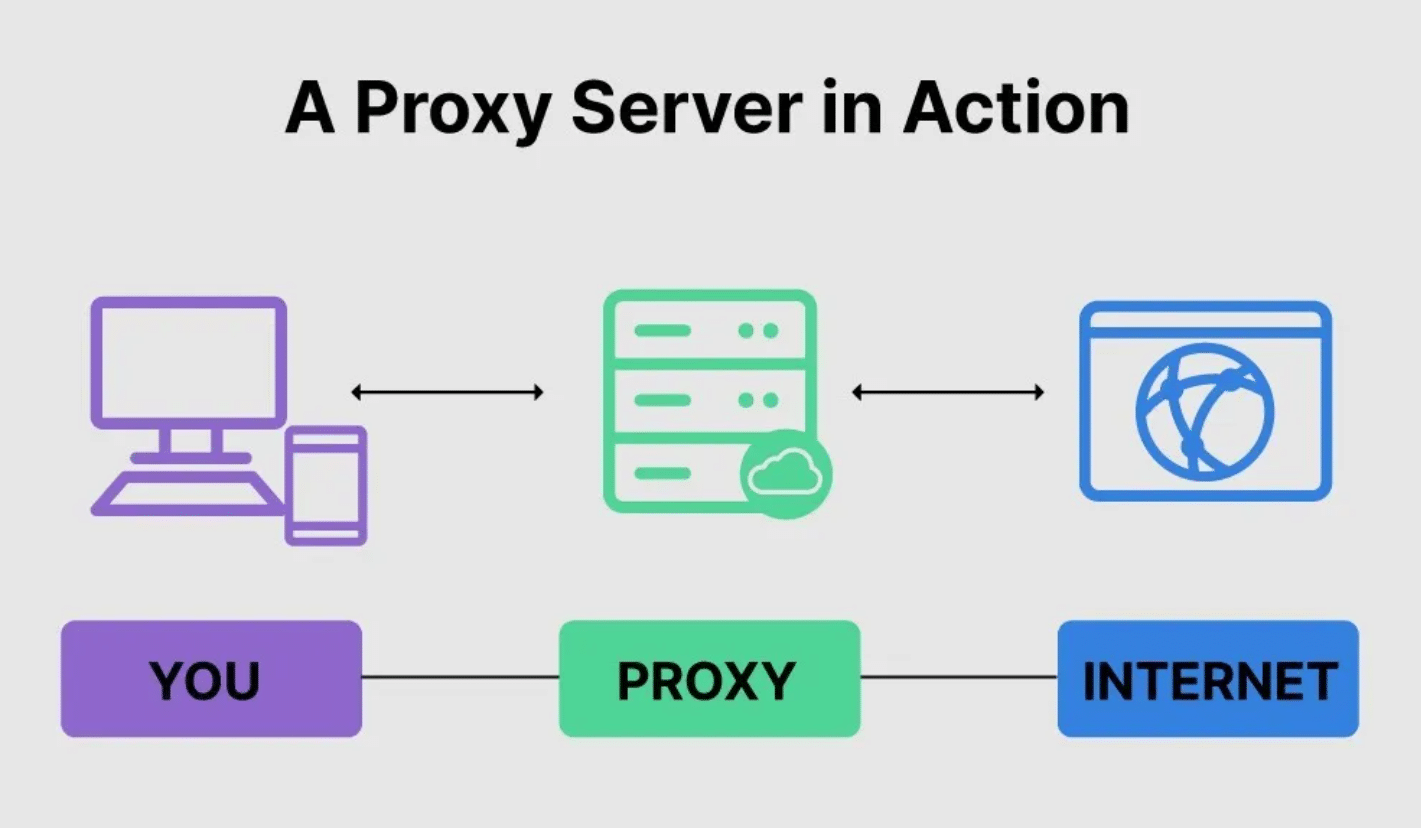
Proxy Service
With a proxy service, the firewall acts as a go-between positioned between your computer and anything that tries to connect to it. A proxy firewall is like a mirror of your computer and detects malicious actors attempting to get through to your device.
Proxy firewalls are a secure solution because of the separation they provide between your computer and the internet. Attackers often need to connect directly to your computer to attack it. Because a proxy is between your computer and the internet, hackers cannot form a direct connection to it, rendering their attack useless.
However, there are applications that proxies are not capable of supporting, and if one of these is important to your business, this could pose an issue. For example, Spotify, Google Play, and QWebView have all been known to have issues when interfacing with a proxy. Proxies also tend to work slower than other types of firewalls, which could reduce throughput and impact important business processes.
Stateful Inspection
A stateful inspection firewall inspects every data packet and compares it against a threat database. During the inspection process, the firewall checks where the data is coming from, the ports it uses, and the applications it is associated with. If the data packet checks out, it is allowed to pass. Otherwise, it is discarded.
Stateful inspection can also collect information about the data packets that go through it and use that to gain more insights into data that may pose potential threats in the future.
How Does a Firewall Protect Data?
Firewall filters keep harmful data outside your computer. Some of the top risks from which firewalls protect your computer include backdoors, denial-of-service (DoS) attacks, macros, remote logins, spam, and viruses.
Backdoors are “doorways” to applications with vulnerabilities that attackers exploit to get inside. This includes operating systems that may have bugs that hackers can use to gain access to your computer.
DoS attacks are executed when a hacker requests permission to connect to a server, and when the server responds, it cannot find the system that made the request. When this is done again and again, the server gets flooded and has to expend so much power to deal with the mass of requests, rendering it unable to meet the needs of legitimate visitors. In some cases, the server has to come offline completely. There are some firewalls that can check whether the connection requests are legitimate, and thus, protect your network from DoS attacks.
Macros refer to scripts run by applications to automate processes. A macro can contain a series of dependent steps that are all launched by one command. Hackers design or purchase macros intended to work within certain applications. A macro can be hidden inside seemingly innocent data, and once it enters your computer, it wreaks havoc on your system. A firewall can detect malicious macros as it examines the packets of data that attempt to pass through.
Remote logins are often used to help someone with a computer issue. However, in the hands of the wrong person, they can be abused, particularly because remote logins provide nearly complete access to your system.
Spam can sometimes include links to malicious websites. These types of sites activate malicious code that forces cookies onto a computer. The cookies create backdoors for hackers to gain access to the computer. Preventing a spam attack is often as simple as not clicking on anything suspicious in an email, regardless of who the sender appears to be. A firewall can inspect your emails and prevent your computer from getting infected.
Viruses, once on a computer, copy themselves and spread to another device on the network. Viruses can be used to do a variety of things, ranging from relatively harmless activity to erasing data on your computer. Firewalls can inspect data packets for viruses, but it is better to use antivirus software in conjunction with a firewall to maximize your security.
Chipin IT Solutions is a leading provider of firewall solutions for businesses of all sizes.
Our firewall solutions are designed to protect your network from malicious attacks and keep your data secure. With Chipin IT Solutions, you can be sure that your network is safe and secure from hackers and other cyber threats. Our firewall solutions provide advanced protection against malware, ransomware, phishing, and other malicious attacks. We also provide real-time monitoring of your network traffic to ensure that all incoming and outgoing traffic is monitored for suspicious activity. With our firewall solutions, you can rest assured that your data is safe from unauthorized access and theft.